FSJ Revirt
FSJ Re Trust
Identity and Access Management
FSJ Revirt from AnyCloud
Backup as a Service (BaaS) and Disaster Recovery as a Service (DRaaS)BaaS: Supporting both VMware and MS Hyper-V virtual machines in the world of virtual platforms. With our agent-based Microsoft Windows & Linux backup solution, we cover both actual devices for endpoints/servers and virtual machines based in hybrid cloud environments like Microsoft Azure, Amazon AWS, Google Cloud and IBM Cloud. Storing your Office 365 environment with us, you will be sleeping better.
Our solution is based on the latest Veeam Availability portfolio. Storing your data in data centres with the highest possible certification on the market.
DRaaS: Using cloud as a disaster recovery site has several advantages. You do not need to build the second datacenter, so you can implement DR significantly faster. With any.cloud, you pay only for what you need. And it is not just about scaling your hardware resources – you only pay for CPUs and RAMs, if your DR is active for those devices. And last, but not least, with any.cloud, you get a reliable partner with massive knowledge and experience. Securing your IT is easy with us.Our experience at any.cloud tells us that for a lot of companies, a timespan of no more than one hour of downtime can be tolerated. That is why we have fine-tuned our DR services to guarantee you 1 hour maximum of recovery time regardless of the size of your business.
Our solution is based on the latest Veeam Availability portfolio. Storing your data in data centres with the highest possible certification on the market.
Our experience at any.cloud tells us that for a lot of companies, a timespan of no more than one hour of downtime can be tolerated. That is why we have fine-tuned our DR services to guarantee you 1 hour maximum of recovery time regardless of the size of your business.
Retrust from AnyCloud, Provided by FSJ Solutions, Powered by IBM
Using IBM Trusteer, you'll be able to establish,
maintain and sustain digital trust with your customers.
The agile cloud platform is built with advanced AI and
machine learning capabilities, giving your company
and your customers a secure digital journey.
FSJ DRM - protect, control and track sensitive documents
FSJ DRM is the most advanced file-based security solution that allows organizations to protect, control and track sensitive documents. The solution is designed to meet the various security requirements of the different stages in the document lifecycle.
Secure Your Data Anywhere it Travels
Track, Control, or Revoke Access
Seamless, Transparent Experience.
FSJ DRM is the most advanced file-based security solution that allows organizations to protect, control and track sensitive documents. The solution is designed to meet the various security requirements of the different stages in the document lifecycle.
Secure Your Data Anywhere it Travels
Track, Control, or Revoke Access
Seamless, Transparent Experience.
Identity and Access Management
An IBM® X-Force® report found that insiders were responsible for 60 percent of attacks surveyed.1 Of those, 15.5 percent were inadvertent actors. Often unwittingly “recruited” to aid the cause of others with malicious intent, they are becoming key players in carrying out highly
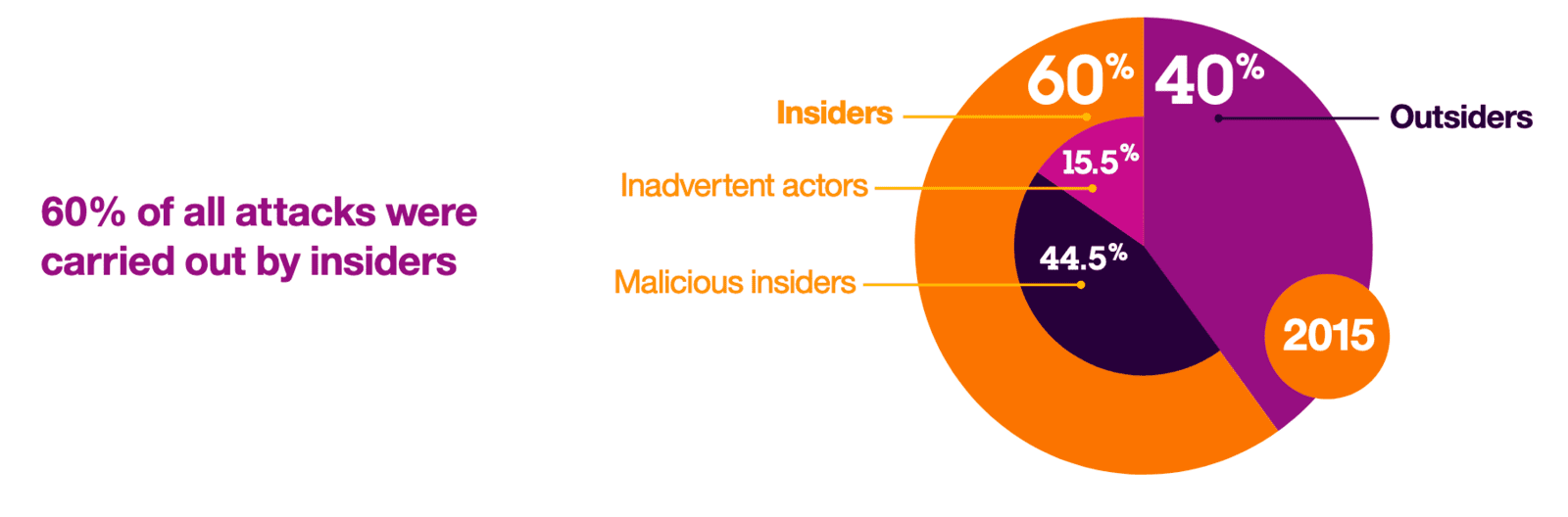
damaging—and potentially prolonged—attacks. And because they’re insiders, they manage to do so without arousing any suspicion, by logging onto a social media site from a corporate network-attached device or opening an email attachment sent by a legitimate-looking business contact.
Then there are the malicious insiders, making up the remaining 44.5 percent, whose actions are not at all innocent. The unsettling truth is that just because they’re considered to be “insiders” doesn’t mean they can be trusted. So it’s important to remember that situations and relationships can change over time—and not always for the better
Our solution helps

Secure your business
Ensure the right people have the right access to resources, for the right purposes.

Enable digital transformation
Make way for business with convenient access to on-premises or cloud-based resources and applications.

Establish trust
Know what’s real with your users and their entitlements across the organization.
We have trained people on IBM’s Identity and Access Management solution and as a methodology we have adopted Info-tech’s approach to help ensure an effective deployment of identity and access management.





